Table of Contents
Introduction
In the ever-evolving landscape of cyber security, staying ahead of threats is most important. To aid organizations in fortifying their digital defenses, the National Institute of Standards and Technology (NIST) has officially announced the release of version 2.0 of its Cybersecurity Framework. This pivotal update promises to bolster cybersecurity practices and align them with emerging challenges and technologies.
Let’s delve into the enhancements, key requirements, and scope of this groundbreaking framework.
Evolution from Version 1.0
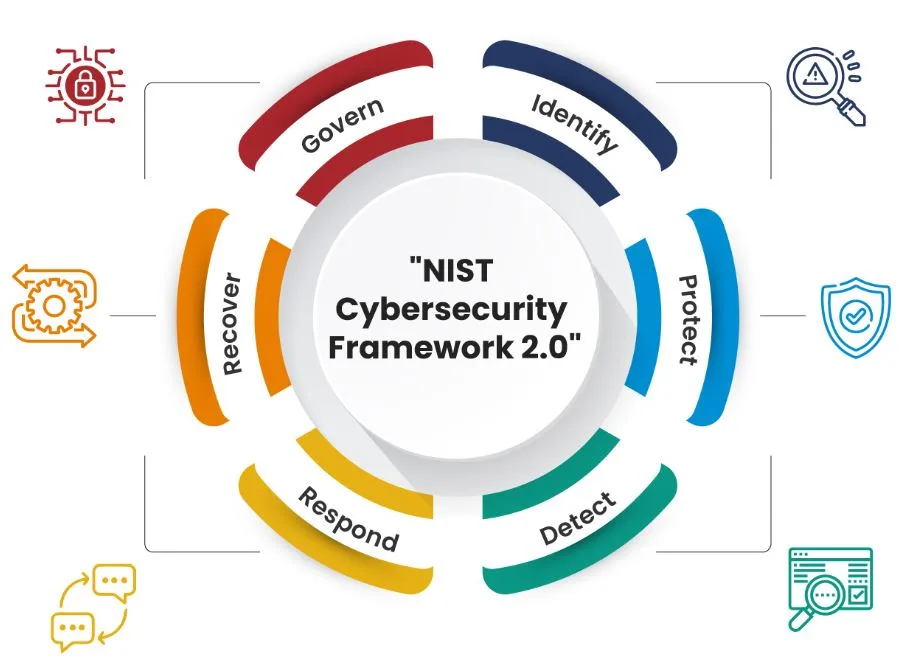
NIST’s Cybersecurity Framework 2.0 builds upon the solid foundation laid by its predecessor, version 1.0. While the core principles of Identify, Protect, Detect, Respond, and Recover remain unchanged, version 2.0 introduces several enhancements to address the evolving threat landscape and technological advancements.
One notable enhancement is the increased focus on supply chain security. Recognizing the interconnected nature of modern business ecosystems, version 2.0 emphasizes the importance of securing the supply chain to mitigate risks stemming from third-party vendors and partners.
Moreover, version 2.0 incorporates feedback from stakeholders and lessons learned from real-world cybersecurity incidents, making it more robust and comprehensive. It embraces a risk-based approach, empowering organizations to tailor cybersecurity practices to their specific needs and risk tolerance levels.
Differentiation and Key Requirements of NIST’s Cybersecurity Framework 2.0
1. Enhanced Guidance and Resources
Version 2.0 of the NIST Cybersecurity Framework offers enhanced guidance and resources to assist organizations in implementing cybersecurity best practices effectively. It provides updated references to other cybersecurity standards and frameworks, facilitating interoperability and alignment with existing initiatives.
2. Supply Chain Risk Management
A significant differentiator of version 2.0 is its heightened emphasis on supply chain risk management. Organizations are encouraged to assess and mitigate risks associated with their supply chain, including third-party suppliers and service providers. This proactive approach helps safeguard against supply chain attacks and disruptions.
3. Integration of Privacy Considerations
Recognizing the growing importance of privacy in the digital age, version 2.0 integrates privacy considerations into its framework. Organizations are encouraged to adopt privacy-enhancing technologies and practices to protect sensitive data and uphold privacy rights.
4. Emphasis on Authentication and Identity Management
Authentication and identity management play a pivotal role in cybersecurity. Version 2.0 highlights the importance of robust authentication mechanisms and identity management practices to prevent unauthorized access and credential misuse.
5. Resilience and Continuity Planning
In the face of cyber threats and disruptions, resilience and continuity planning are essential. Version 2.0 underscores the importance of proactive measures such as incident response planning, business continuity management, and disaster recovery to ensure business resilience in the event of a cybersecurity incident.
Key Requirements and Scope

1. Identify
The “Identify” function remains the cornerstone of the NIST Cybersecurity Framework. Organizations are tasked with understanding and managing cybersecurity risks by identifying assets, assessing vulnerabilities, and establishing risk management processes.
2. Protect
Under the “Protect” function, organizations are required to implement safeguards to protect against cybersecurity threats. This includes deploying access controls, encrypting sensitive data, and implementing security awareness training programs for employees.
3. Detect
The “Detect” function focuses on proactively identifying cybersecurity incidents. Organizations are encouraged to deploy monitoring systems, conduct regular security assessments, and establish incident detection and response procedures to detect and respond to threats effectively.
4. Respond
In the event of a cybersecurity incident, the “Respond” function guides organizations in effectively responding to and mitigating the impact of the incident. This includes activating an incident response team, containing the incident, and coordinating with relevant stakeholders and authorities.
5. Recover
The “Recover” function outlines steps to recover from a cybersecurity incident and restore normal operations. This includes conducting post-incident reviews, updating recovery plans, and implementing measures to prevent future incidents.
Implementation Steps
1. Assessment and Gap Analysis:
Begin by conducting a comprehensive assessment of your organization’s current cybersecurity posture and practices. Identify gaps and areas for improvement based on the key requirements outlined in the NIST Cybersecurity Framework 2.0.
2. Establish Governance and Leadership:
Appoint a dedicated cybersecurity team or designate existing personnel to oversee the implementation of the framework. Establish clear roles, responsibilities, and reporting structures to ensure effective governance and leadership.
3. Tailoring the Framework:
Customize the framework to suit your organization’s specific needs, risk profile, and industry requirements. Prioritize key areas such as supply chain security, privacy considerations, authentication, and resilience planning based on your organization’s priorities and risk tolerance levels.
4. Implementation of Controls:
Implement the recommended controls and best practices outlined in the framework across all relevant areas of your organization. This may include deploying technical solutions, updating policies and procedures, and conducting employee training and awareness programs.
5. Monitoring and Continuous Improvement:
Establish mechanisms for ongoing monitoring, measurement, and evaluation of your cybersecurity practices. Implement regular assessments, audits, and reviews to identify emerging threats and vulnerabilities and make necessary adjustments to your cybersecurity strategy.
6. Incident Response Planning:
Develop and document robust incident response plans and procedures in alignment with the framework’s guidelines. Ensure that your organization is prepared to detect, respond to, and recover from cybersecurity incidents effectively.
7. Collaboration and Information Sharing:
Foster collaboration and information sharing both internally and externally to enhance cybersecurity resilience. Engage with industry peers, government agencies, and cybersecurity organizations to stay informed about emerging threats and best practices.
8. Training and Awareness:
Provide regular cybersecurity training and awareness programs for employees at all levels of your organization. Educate personnel about their roles and responsibilities in maintaining cybersecurity and encourage a culture of vigilance and accountability.
By following these implementation steps and embracing the key requirements outlined in the NIST Cybersecurity Framework 2.0, organizations can strengthen their cybersecurity posture and better protect against evolving threats in today’s digital landscape.
Conclusion
NIST’s Cybersecurity Framework 2.0 represents a significant milestone in the ongoing effort to enhance cybersecurity practices and resilience. By incorporating feedback from stakeholders and addressing emerging challenges such as supply chain security and privacy considerations, version 2.0 equips organizations with the tools and guidance needed to navigate the complex cybersecurity landscape effectively.
By embracing the key requirements and principles outlined in the framework, organizations can bolster their cybersecurity posture and safeguard their digital assets against evolving threats.
Frequently Asked Questions (FAQ)
1. What is NIST’s Cybersecurity Framework 2.0?
– NIST’s Cybersecurity Framework 2.0 is a set of guidelines, best practices, and standards designed to help organizations improve their cybersecurity posture. It provides a flexible framework for managing and reducing cybersecurity risks, aligning with business objectives, and enhancing resilience against cyber threats.
2. What are the key differences between version 1.0 and version 2.0 of the Cybersecurity Framework?
– Version 2.0 of the Cybersecurity Framework builds upon the foundation laid by version 1.0 and introduces several enhancements. These include increased focus on supply chain security, integration of privacy considerations, emphasis on authentication and identity management, and enhanced guidance and resources.
3. How does the Cybersecurity Framework 2.0 help organizations manage supply chain risks?
– The Cybersecurity Framework 2.0 emphasizes the importance of supply chain risk management by encouraging organizations to assess and mitigate risks associated with their supply chain partners and vendors. It provides guidance on implementing controls to secure the supply chain and mitigate the impact of supply chain attacks.
4. How does the Cybersecurity Framework 2.0 address privacy considerations?
– Version 2.0 of the Cybersecurity Framework integrates privacy considerations into its framework, recognizing the growing importance of privacy in the digital age. It encourages organizations to adopt privacy-enhancing technologies and practices to protect sensitive data and uphold privacy rights.
5. What role does authentication and identity management play in the Cybersecurity Framework 2.0?
– Authentication and identity management are essential components of cybersecurity. Version 2.0 of the Cybersecurity Framework highlights the importance of robust authentication mechanisms and identity management practices to prevent unauthorized access and credential misuse.
6. How can organizations implement the Cybersecurity Framework 2.0?
– Organizations can implement the Cybersecurity Framework 2.0 by following a series of steps, including assessment and gap analysis, establishment of governance and leadership, tailoring the framework to their specific needs, implementation of controls, monitoring and continuous improvement, incident response planning, collaboration and information sharing, and training and awareness programs.
7. Is the Cybersecurity Framework 2.0 mandatory for organizations?
– The Cybersecurity Framework 2.0 is voluntary and does not impose mandatory requirements on organizations. However, many organizations choose to adopt the framework as a best practice for managing cybersecurity risks and improving their cybersecurity posture.
8. Is the Cybersecurity Framework 2.0 applicable to all types of organizations?
– Yes, the Cybersecurity Framework 2.0 is designed to be flexible and scalable, making it applicable to organizations of all sizes and across various industries. Whether you’re a small business, a multinational corporation, a government agency, or a nonprofit organization, you can benefit from implementing the framework.
9. Where can I find more information about the Cybersecurity Framework 2.0?
– More information about the Cybersecurity Framework 2.0, including guidance documents, implementation resources, and frequently asked questions, can be found on the official website of the National Institute of Standards and Technology (NIST).
10. Can organizations use the Cybersecurity Framework 2.0 alongside other cybersecurity standards and frameworks?
– Yes, organizations can use the Cybersecurity Framework 2.0 alongside other cybersecurity standards and frameworks. The framework provides references to other standards and frameworks, facilitating interoperability and alignment with existing cybersecurity initiatives.
Read more on https://cybertechworld.co.in for insightful cybersecurity related content.




















I loved as much as you will receive carried out right here The sketch is attractive your authored material stylish nonetheless you command get got an impatience over that you wish be delivering the following unwell unquestionably come more formerly again since exactly the same nearly a lot often inside case you shield this hike
I really enjoyed what you have accomplished here. The outline is elegant, your written content is stylish, yet you seem to have acquired a bit of apprehension over what you aim to convey next. Undoubtedly, I will revisit more frequently, just as I have been doing nearly all the time in case you sustain this upswing.
What a fantastic resource! The articles are meticulously crafted, offering a perfect balance of depth and accessibility. I always walk away having gained new understanding. My sincere appreciation to the team behind this outstanding website.
I just could not leave your web site prior to suggesting that I actually enjoyed the standard information a person provide on your guests? Is going to be back ceaselessly in order to check out new posts
Your article helped me a lot, is there any more related content? Thanks! https://accounts.binance.com/ES_la/register-person?ref=T7KCZASX