
Table of Contents
Context
Imagine this: an attacker sneaks onto an employee’s laptop, trying to run malicious code or steal data. What happens next? In a well-oiled cybersecurity monitoring and response setup, the system doesn’t just sit there—it springs into action with a simple, streamlined flow. Alerts pop up centrally, automation kicks in to contain the threat, and a human analyst wraps it up. No chaos, no endless email chains.
This four-step process—powered by EDR, SIEM, SOAR, and smart analysts—turns potential disasters into quick wins. As a CISO in India’s insurance world, I’ve seen how this keeps sensitive customer data safe without overwhelming your SOC team. Let’s break it down step by step, like explaining it over coffee, emphasizing the importance of cybersecurity monitoring and response.
Step 1: EDR – Your Endpoint Watchman
Endpoint Detection and Response (EDR) is the frontline guard on every laptop, server, and device. It constantly scans for red flags: suspicious files downloading, weird processes launching, or unusual behavior like ransomware encrypting files.
- What it does: Spots threats in real-time and acts fast—blocks the bad file, isolates the device from the network, or quarantines the process.
- Why it matters: In a life insurance firm, an infected claims processor laptop could expose policyholder PII. EDR stops it before data walks out the door.
- Real-world example: Think of that phishing email with a fake invoice. EDR sees the executable trying to phone home and slams the door.
Once it detects something, EDR logs every detail and fires off an alert. No more waiting for manual scans—this is proactive hunting. Tools like CrowdStrike or Microsoft Defender shine here, integrating seamlessly with your IRDAI-compliant setups.
Step 2: SIEM – The Central Log Brain
Security Information and Event Management (SIEM) pulls it all together. It grabs logs from EDR, firewalls, cloud services, and even your insurance apps, dumping them into one searchable dashboard.
- Key superpower: Correlation. One failed login? Meh. But 50 from a new IP in Russia, plus traffic spikes to shady domains? That’s an incident alert blasting to your SOC.
- In action: SIEM spots patterns humans might miss, like a brute-force attack ramping up during off-hours.
- Insurance twist: Tune it for DPDP compliance—flag unusual access to customer health records or policy databases.
SIEM isn’t just a log hoarder; it’s the brain that prioritizes “this laptop’s compromised” over “routine printer jam.” Splunk or Elastic are go-to, feeding straight into the next step.
Step 3: SOAR – Automation Engine
Security Orchestration, Automation, and Response (SOAR) reads those SIEM alerts and runs pre-built playbooks automatically. No analyst clicking buttons at 2 AM.
| Action | What It Does | Why Useful |
| Block IP | Blacklists attacker’s source instantly | Stops lateral movement |
| Disable Account | Locks risky user until review | Prevents privilege escalation |
| Notify Team | Pings Slack/Teams/email | Gets humans in the loop fast |
| Snapshot Device | Backs up evidence for forensics | Aids IRDAI reporting |
Platforms like Palo Alto Cortex XSOAR or Swimlane make this plug-and-play, scaling for Indian enterprises with data localization needs.
Step 4: Analyst – The Human Touch
Automation handles the grunt work, but analysts make the final call. They dive into SIEM/SOAR dashboards for context.
- Their role: Verify if it’s a false positive (e.g., legit software update), tweak actions, document for audits, or escalate to malware reverse-engineering.
- Closing the loop: Update tickets, notify affected users (“Your laptop’s clean now”), and feed lessons back to tune EDR rules.
- Efficiency hack: With SOAR handling basics, analysts focus on strategy—not firefighting.
In my experience prepping board reports, this human oversight ensures compliance gold—every incident logged, lessons learned.
Visualizing the Flow: Key Flowcharts
Here are two flowcharts to make it crystal clear. First, the high-level 4-step overview:
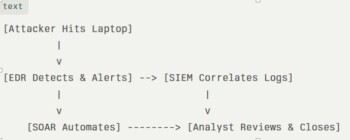
Second, a detailed decision tree for incident handling:

These visuals fit right into your InfoSec committee slides—simple, actionable.
Why This Works for Indian CISOs
In regulated sectors like insurance, where IRDAI demands rapid response and DPDP insists on breach notifications within 72 hours, this flow shines. It cuts mean-time-to-respond (MTTR) from hours to minutes, scales without ballooning headcount, and generates audit-ready reports. Start small: pick one tool stack (EDR+SIEM+SOAR), pilot on critical endpoints, then expand.
Disclaimer: Shared for educational purposes only—adapt to your environment and consult experts.
Read more on https://cybertechworld.co.in for insightful cybersecurity related content.



















