
Table of Contents
Introduction
In the vast landscape of cybersecurity, every component plays a crucial role in fortifying the digital infrastructure. Among these components, the Domain Name System Security Extensions (DNSSEC) stands as a vital mechanism for ensuring the integrity and authenticity of DNS data. However, recent discoveries have shed light on a concerning vulnerability within DNSSEC known as KeyTrap.
This blog aims to delve into the depths of KeyTrap vulnerability, its implications, and propose effective countermeasures to mitigate its risks.
Understanding KeyTrap Vulnerability
DNSSEC operates on a system of cryptographic keys to sign and verify DNS data, thereby enhancing its security. However, KeyTrap represents a critical flaw within this framework. Essentially, KeyTrap occurs when a malicious actor manipulates the DNSSEC key rollover process to gain unauthorized access or control over DNS records.
The vulnerability arises during the key rollover process, where new cryptographic keys are introduced to replace the old ones. Attackers exploit this transition period by intercepting the communication between DNS resolvers and authoritative servers, thereby hijacking the DNS records. This manipulation allows them to redirect legitimate traffic, leading to potential DNS spoofing, pharming attacks, or even complete denial of service.
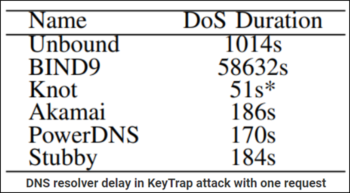
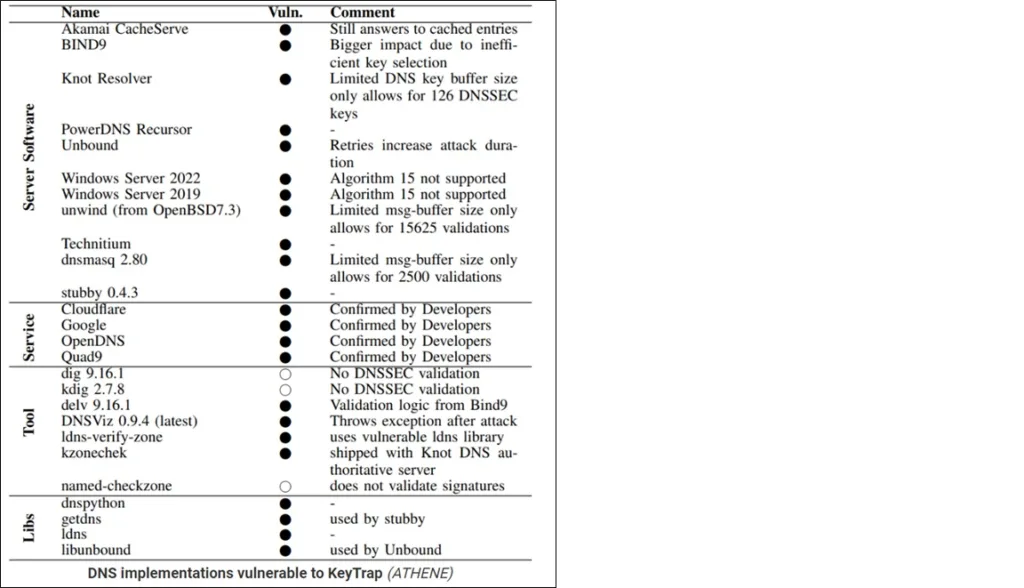
Implications of KeyTrap
The ramifications of KeyTrap vulnerability extend far beyond mere data manipulation. Infiltration of DNS records not only compromises the integrity of digital communications but also undermines the trust and reliability of the entire DNS infrastructure. With DNS serving as a fundamental component of internet functionality, any compromise in its security can have widespread consequences, including data breaches, identity theft, and financial losses.
Countermeasures Against KeyTrap
To combat the threat posed by KeyTrap vulnerability, organizations and network administrators must implement robust countermeasures.
Here are some effective strategies to safeguard DNSSEC against exploitation:
1. Continuous Monitoring and Auditing: Regular monitoring of DNSSEC infrastructure can help detect any anomalies or unauthorized changes in DNS records. Automated auditing tools can assist in identifying discrepancies during key rollover processes, enabling prompt intervention in case of suspicious activities.
2. Secure Key Management Practices: Implementing secure key management practices is paramount in mitigating KeyTrap vulnerability. This includes maintaining strict access controls, regularly rotating cryptographic keys, and storing them in secure, tamper-proof hardware security modules (HSMs) to prevent unauthorized access or tampering.
3. Implementing DNS Response Rate Limiting (DNS RRL): DNS Response Rate Limiting (DNS RRL) is a technique that helps mitigate DNS amplification attacks by limiting the rate of DNS responses to queries from suspicious sources. By implementing DNS RRL, organizations can minimize the impact of DNS-based attacks, including those exploiting KeyTrap vulnerability.
4. Utilizing DNS Firewalls: DNS firewalls play a crucial role in filtering and inspecting DNS traffic, thereby preventing malicious activities, including DNS spoofing and cache poisoning. By deploying DNS firewalls at strategic points within the network infrastructure, organizations can effectively block unauthorized attempts to exploit KeyTrap vulnerability.
5. Implementing Domain-based Message Authentication, Reporting, and Conformance (DMARC): DMARC is an email authentication protocol that helps prevent email spoofing and phishing attacks by enabling domain owners to specify how their emails should be authenticated. By implementing DMARC policies, organizations can reduce the risk of attackers exploiting DNS vulnerabilities, including KeyTrap, to launch phishing campaigns or impersonate legitimate entities.
6. Regular Security Updates and Patch Management: Keeping DNSSEC software and associated components up-to-date with the latest security patches is essential to address known vulnerabilities and mitigate emerging threats, including KeyTrap. Organizations should establish robust patch management processes to ensure timely deployment of security updates across their infrastructure.
Conclusion
KeyTrap vulnerability poses a significant threat to the integrity and security of DNSSEC, potentially leading to severe consequences for organizations and internet users worldwide. However, by implementing proactive security measures and adopting best practices, organizations can effectively mitigate the risks associated with KeyTrap and enhance the resilience of their DNS infrastructure.
Through continuous monitoring, secure key management, and the deployment of appropriate security controls, we can collectively fortify DNSSEC against exploitation and uphold the trust and reliability of the internet’s foundational protocols. Let us remain vigilant and proactive in safeguarding our digital ecosystem against evolving cyber threats.
Read more on https://cybertechworld.co.in for insightful cybersecurity related content.




















Your article helped me a lot, is there any more related content? Thanks!
Thank you for another wonderful post. Where else could anyone get that kind of info in such an ideal way of writing? I’ve a presentation next week, and I am on the look for such information.